Prevent Zero Day Attacks
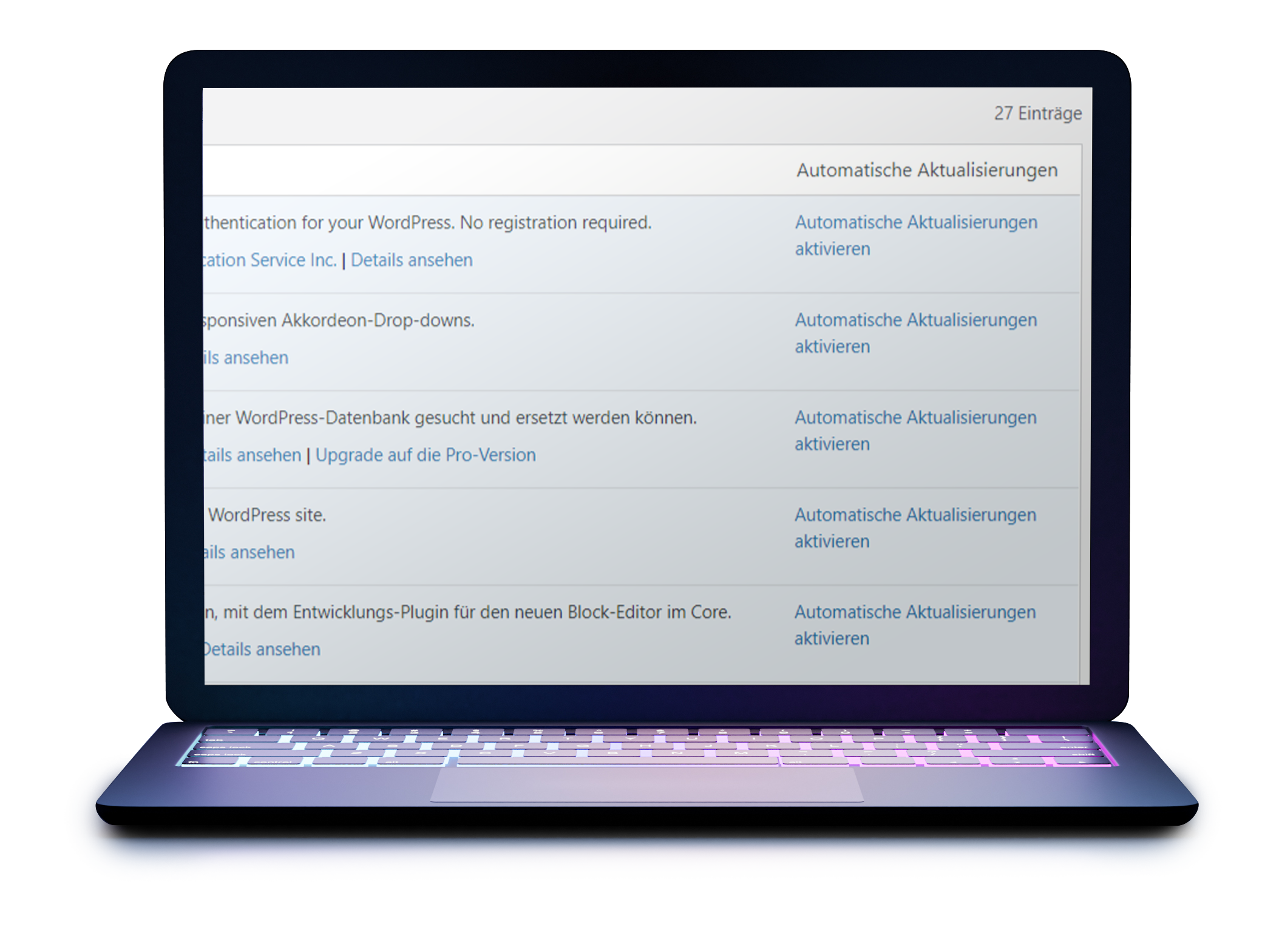
Automatic updates
WordPress is safer than the competition. This is also due to the fact that security updates are installed fully automatically.
You can also enable this for individual plugins. Especially plugins are regularly affected by security vulnerabilities – automatic updates thus usually effectively prevent zero-day attacks.
At the same time, it can be dangerous to install plugin updates fully automatically on a live website without prior testing.
While an update of WordPress itself has usually been extensively tested, the stability varies depending on the plugin. Here you need to weigh the stability of the website against this security feature.
If necessary, only enable those plugins for automatic updates that are particularly stable for you and exclude those that have had problems with updates in the past.
Prevent total loss
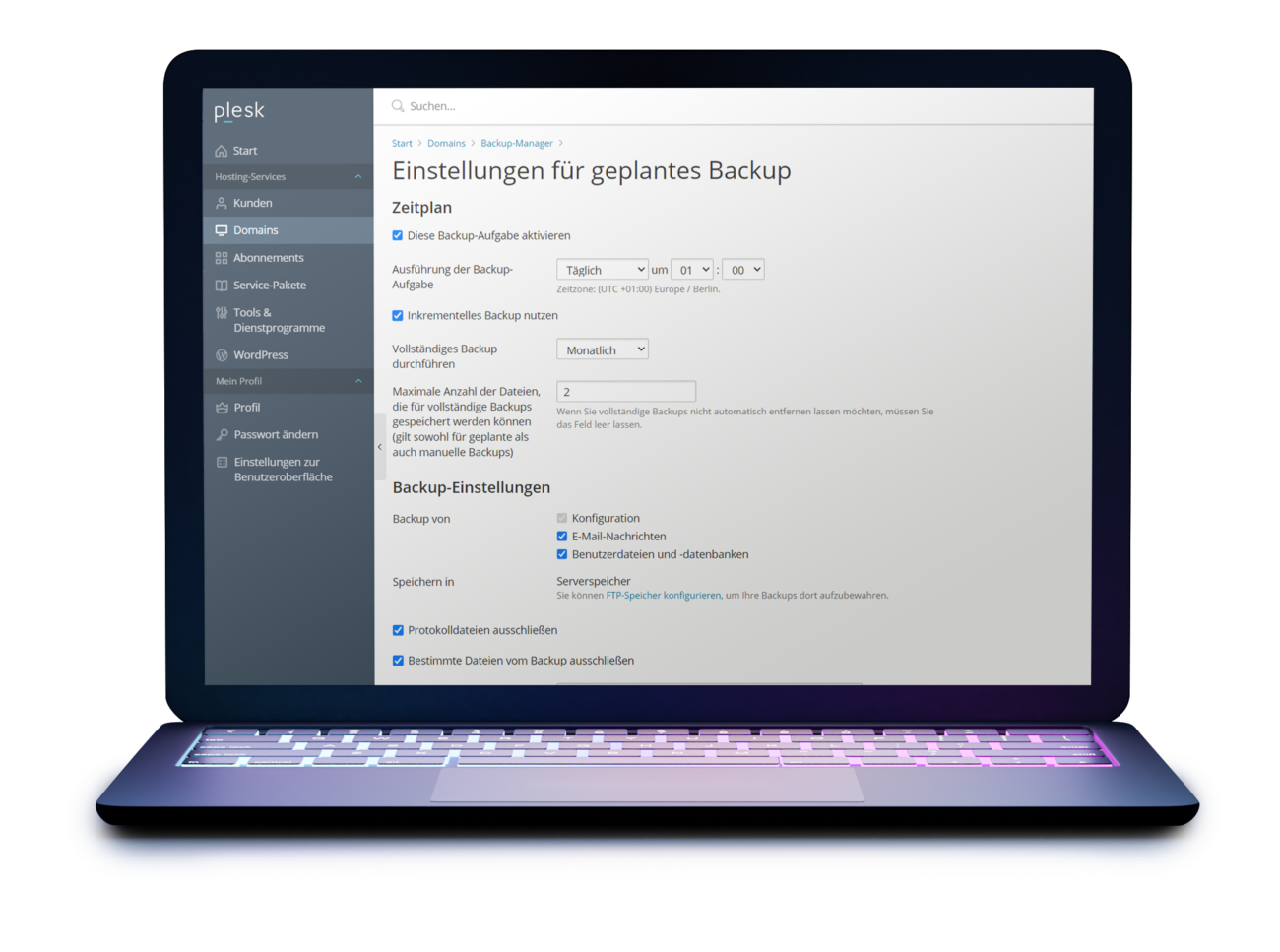
Automatic backups
We recommend avoiding WordPress backup plugins – in our experience, they repeatedly lead to critical problems and bloated WordPress installations. According to the Separation of Concerns approach, a system should not create backups for itself.
Use external tools, we recommend the possibilities of the server software Plesk. Ideally, set up the backup plan to create daily, incremental backups.
Many web hosts also offer their own backups on dedicated backup servers, sometimes at an additional cost. That is good and sensible. However, backups should always be redundant to have an additional layer of security. You should be able to create and restore backups yourself – even parts of them, i.e. individual directories, files or databases.
For our web hosting customers, we therefore combine the backups at the server level and the individual ones at the customer level by default.
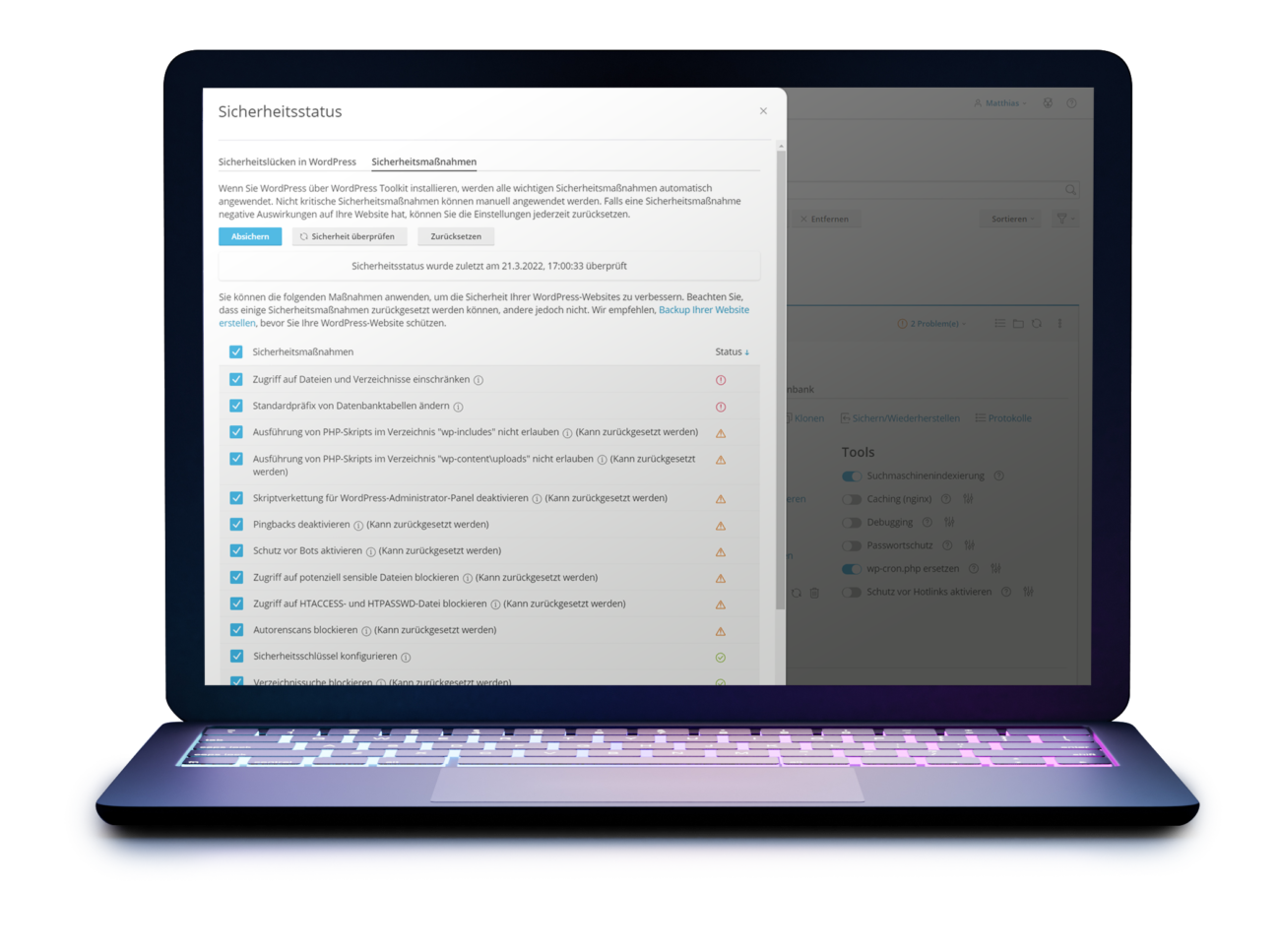
Optimize access rights
Settings
Many servers are configured in such a way that as many software as possible works on them. This often results in non-optimal security settings for WordPress systems.
Therefore, optimize file access rights and classic attack vectors at the server level.
With Plesk’s WordPress tools, you can easily secure your WordPress installation, otherwise ask your technical service provider to check access rights.
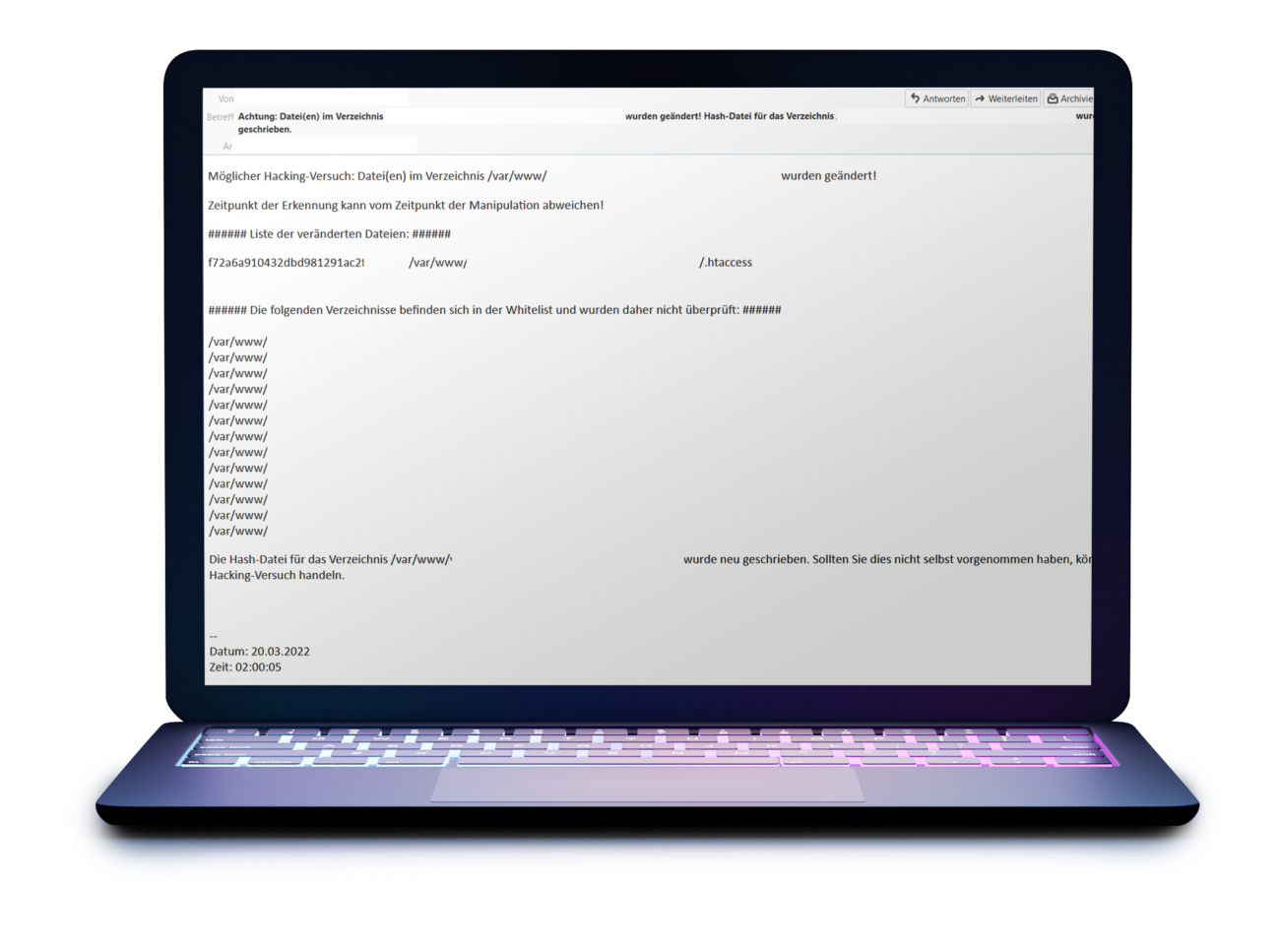
Detect and limit hacking
Monitor file changes
Once the child has fallen into the well, it is important to act quickly. If your WordPress website has been hacked, two areas can be affected: the database or the files on the server.
Changes in the database could be, for example, changed posts and pages with which hackers can distribute malicious code or play out advertisements. Changes are more difficult to reliably record here, so we recommend that you simply install an intact backup of the database after a successful hacking attack.
File changes, on the other hand, are easier to monitor. Especially changed .php or .htaccess files – without an update being applied – are a strong warning signal for a hacking attack.
For some customers, we therefore use a script that regularly – for example every 15 minutes – monitors the WordPress directory for file changes.
If changes are detected, an e-mail with a list of changed files is sent. In this way, the number and time of the affected files can be effectively limited.
This significantly reduces the effort required to analyze, fix, and restore the site after a successful hack.
Fire & Forget or Snake Oil?
All in One Security Plugins
Firewall and virus scanner plugins have a fundamental problem: they are part of the system to be protected.
Even if the previously published or known vulnerability in NinjaFirewall was not critical, this shows that these plugins themselves can bring security gaps into the system.
In addition, these plugins also have an effect on the performance of the system and it is another plugin that must be taken into account in the WordPress updates.
Similar to antivirus programs for Windows, the actual protection of All in One Security Plugins is difficult to assess, useless or harmful. We recommend a better alternative in the next chapter.
Firewall & CDN
Cloudflare
Rarely has a security tool been as much fun for us as Cloudflare. The setup effort is intuitive and manageable for technicians.
The biggest advantage is that Cloudflare already protects the website at the DNS level. Attacks are therefore already fended off before they reach the WordPress server. Cloudflare not only fends off potential attack attempts, but also malicious bots and DDOS attacks.
Best of all, the basic version for Cloudflare is free of charge and already offers very good protection. We recommend booking the Pro variant for $20 a month for the convenient PageSpeed accelerations and advanced bot detection.
Useless at best
Hide WP admin directory
The popular plugin Hide my WP allows you to hide the /wp-admin/ directory. We cannot recommend the use.
For hackers, hiding the WP admin directory is not a big hurdle. The changed directory can still be found. It is often argued that this is only one of many building blocks to make attacks more difficult overall.
Unfortunately, every additional plugin in WordPress is another attack vector for hackers and potentially brings its own security vulnerabilities. The plugin Hide my WP last had a critical security vulnerability in November 2021, the plugin WPS Hide Login already several (1) (2).
Instead of increasing website security, a door is opened for hackers.
Avoid insecure passwords
Password Policies
Secure passwords are fundamental to increasing the security of a website. But the requirements should also be implemented.
To enforce this, a Password Policy Plugin is recommended. Secure passwords are as long as possible and you don’t even try to remember them yourself – just use a password manager for this.

Effective protection
2-factor authentication
No matter whether the password was too simple or it was otherwise tapped: Thanks to the 2-factor authentication, effective protection against unauthorized access is possible.
In addition to the normal login data, a token is requested that is retrieved via a separate smartphone app – similar in technology to online banking.
We recommend the free provider 2FAS.
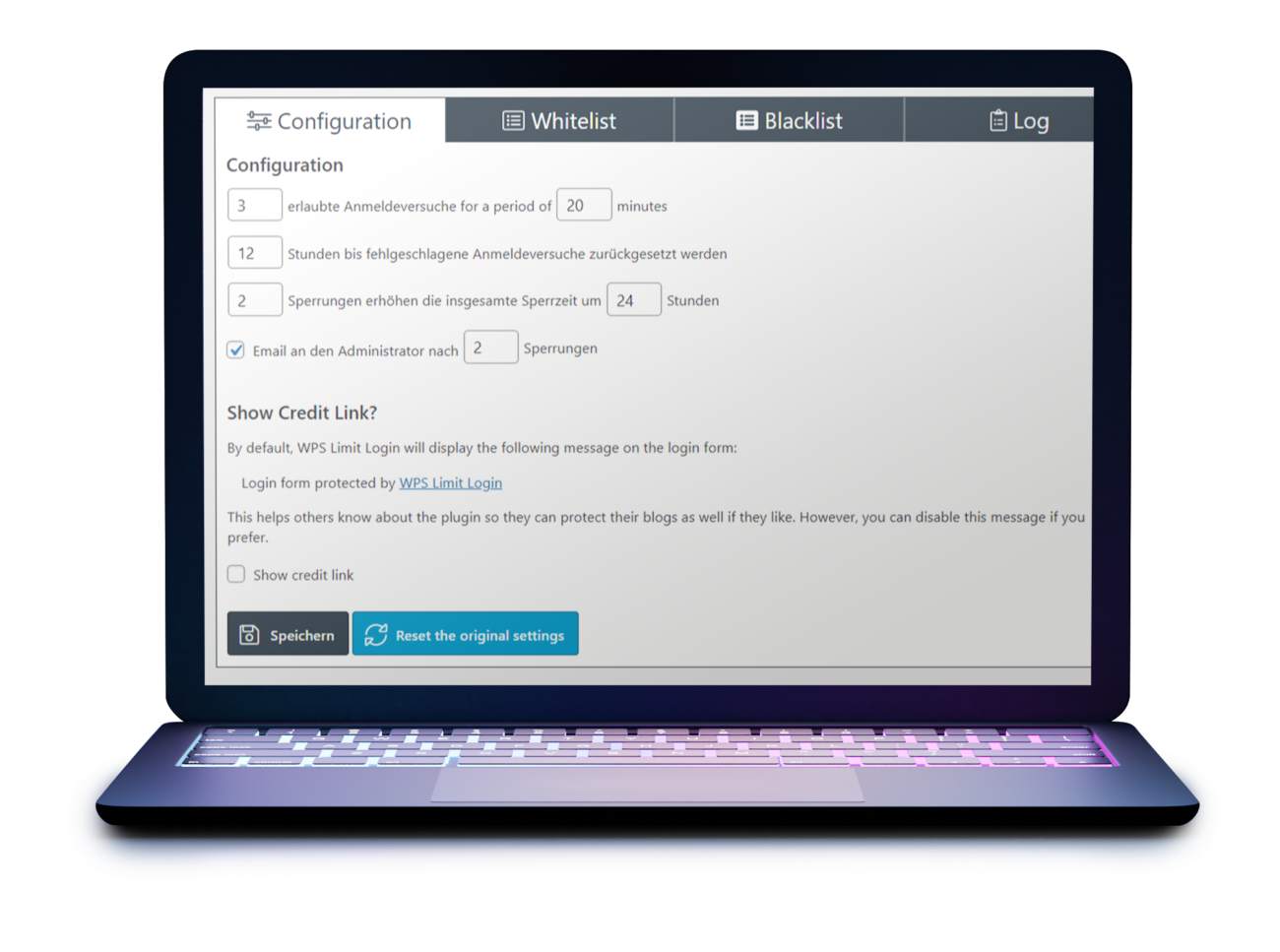
Taking the wind out of your sails
Limit login attempts
Automated scripts can try out thousands of login combinations per second. You can effectively prevent this by limiting the number of login attempts.
For example, use the free plugin WPS Limit Login.
Safe is safe
WordPress websites are real targets for hacking attacks. No system is perfectly secured, every system offers known and unknown security vulnerabilities.
With the measures we have outlined, you can combat and complicate multiple attack vectors: DDOS attacks, phishing, brute force and many more.
Setting up the various tools and services is now easy and not a major challenge for technicians. Perhaps even more importantly, the website remains easily accessible and operable for users, as the measures are specifically effective against classic attack patterns by hackers.
Our recommendation
Take the time to gain effective security while refraining from ineffective measures.